
In the information society, all kinds of information can be easily duplicated.We are now in an age where that information can be delivered regardless of location or time.
This evolution of the environment has enriched our lives and brought great opportunities for business and many encounters.
At the same time, it can be said that we have entered an era in which it is difficult to reliably protect personal information.While it is useful for diversifying various changes and speeding up analysis and judgment, it is difficult to distinguish whether the information that influences judgment is biased information influenced by specific interests or objective facts. It overshadows its usefulness.
By promoting the appropriate handling of personal information in this era, Universe Club not only contributes to the protection of personal information, but also makes thoroughgoing efforts to protect personal information and provides customers with peace of mind. I'm going to try to make you feel more safe than ever.
![]() How the JAPHIC mark was acquired
How the JAPHIC mark was acquired

In Japan, the Personal Information Protection Law has been amended several times.What can Universe Club itself do?Returning to the starting point, what should be done about more strict protection of personal information and handling?I've been thinking about it.
Among them, the personal information protection system that we are doing in our company has been examined and certified from the perspective of a third-party organization, and we are operating as a corporation, so that we can provide "reliability" to those who use it. And I decided to acquire it in order to feel "safety" and "safety".
![]() What is the JAPHIC mark system?
What is the JAPHIC mark system?
The JAPHIC mark certification system complies with the "Act on the Protection of Personal Information" (Act No. 15 of May 5, 30) and maintains and operates a system to take appropriate protection measures for personal information. It is a system that examines businesses that do so and approves the use of the JAPHIC mark to that effect.
![]() Access control
Access control
Introduced smart key "SESAME"

We use a smart key system to manage all office keys and entry/exit.
Remote control is also possible, so you can quickly respond to situations such as forgetting to lock the door, and you can also detect suspicious comings and goings.
●Unlocking and locking all with a smartphone

To unlock or lock, just tap the app or touch the sticker with your phone!
The security effect is enhanced by separating the authority of the door that any employee can enter and the door of the management area.
In addition, a log is kept each time the door is unlocked, so you can easily find out who entered and left when.
You can also check the entry and exit of the room on the management screen
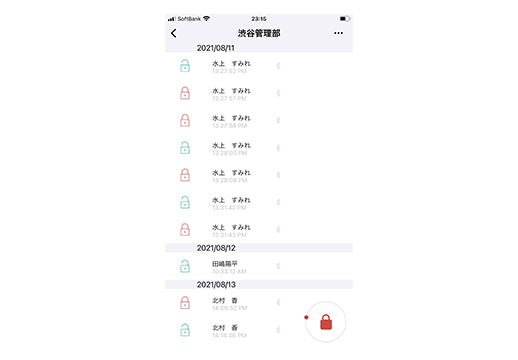
On the management screen, you can check who entered and left the room and when.
Clear management prevents the loss of personal information before it happens, and also clarifies the cause of accidents related to personal information.
![]() How to process paper media - Shredder -
How to process paper media - Shredder -
● Shredder is required for highly confidential items

Use shredders as primary processing for confidential documents.
Items with high confidentiality, such as personal information, will be immediately shredded.
![]() Processing method of paper media - dissolution processing -
Processing method of paper media - dissolution processing -
Put documents to be dissolved in a locked cabinet

Documents that are not subject to immediate shredding will be dissolved.
Dedicated boxes for dissolution are stored in locked cabinets.
● Stored only by authorized staff

Temporarily store confidential documents, etc. to be disposed of in special boxes in cabinets that can only be opened by authorized personnel.
Put your documents in this box

Envelopes for mail addressed to our company are also subject to dissolution.
Almost all paper media handled by our company are disposed of in this way.
Request a dissolution box from a contractor and incinerate it

Dedicated dissolution boxes are designed to be collected and disposed of by specialists after a certain period of time, even if the amount is small.
![]() System for deleting information on PCs
System for deleting information on PCs
● Initialize the data in the PC
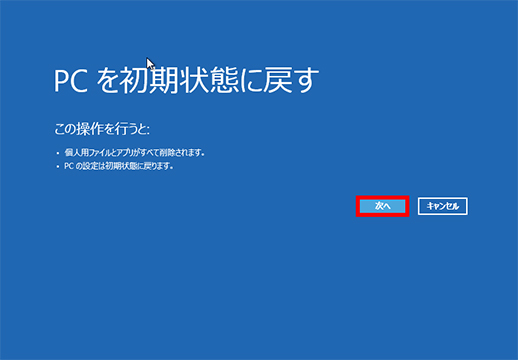
First, the data itself in the PC is digitally deleted.
Then initialize the PC itself.
●Take out the hard disk

Take out the hard disk of the PC you no longer use and disconnect everything including cables.
Make the hard disk unrecoverable

Send the HD to a professional and make it unrecoverable.
![]() Two-factor authentication for all apps you use
Two-factor authentication for all apps you use
● When logging in, enter your e-mail address
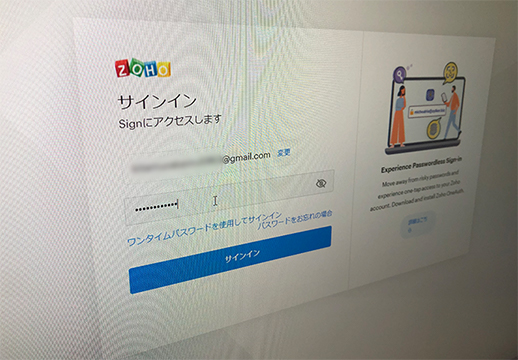
In the case of the application that we use on our system, we have implemented two-step authentication to strengthen security by entering the registered address and setting the authentication notification to be sent to your smartphone.
●Two-step authentication is fingerprint authentication with the person's smartphone
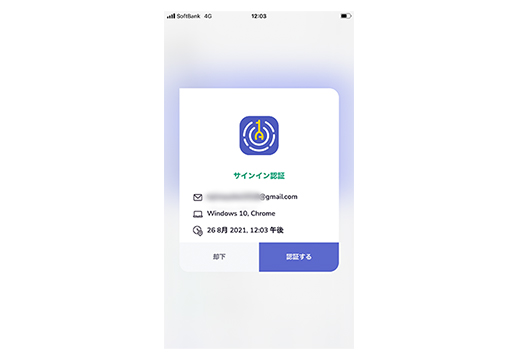
Security is protected by performing two-factor authentication on your smartphone for each account and issuing fingerprint authentication or one-time password.
●Ensure security for the password itself

There is a password management app in the application of our system.
By using this
- Share system login information without employees knowing ID and PW (sharing can be set or canceled at any time)
- Immediately block login privileges for retired employees
This makes it possible to efficiently share information within the company and to limit information leaks and unauthorized use with a high degree of accuracy.
![]() SSL certificate
SSL certificate
●Encrypted communication with users

SSL (Secure Sockets Layer) is a mechanism for encrypting exchanges (communications) between a website and a user browsing the website.
Everything related to the business of Universe Club is on this SSL-certified page.
![]() In the event of cyber risk or information leakage
In the event of cyber risk or information leakage
● About countermeasures and compensation

Even in the unlikely event that something should happen, our club has insurance against cyber risks and information leaks.As for the contents of the insurance we have, by entering the plan of compensation amount for a wide range of damage, regardless of external factors, internal factors, etc., the cost of compensation damage to the customer is generous. I will do it.
![]() Employee training on personal information
Employee training on personal information
●Regular training on personal information protection

Training for new graduates, training for managers, etc. are held every year as annual events.
In addition, when necessary, such as when laws are amended, we provide training opportunities on an irregular basis, and we are working to deepen our understanding of personal information protection throughout the company.
●Personal information protection training app within the system

In addition to the above classroom training, we have installed a training app in our own system.
Through e-learning and other means, we have established a system that allows employees to set their own schedules and learn freely.


